
- High Assurance
- Enterprise EV
- Wildcard SSL/TLS
- Multi-domain UCC/SAN
- Enterprise EV UCC/SAN
- Code Signing
- EV Code Signing
- Secure Email (S/MIME)
- Client Authentication
- eSigner Document Signing
- NAESB Certificates
Select Language

We hope you will find the Google translation service helpful, but we don't promise that Google's translation will be accurate or complete. You should not rely on Google's translation. English is the official language of our site.
Configuring Client Authentication Certificates in Web Browsers
- SSL.com Support Team
- May 5, 2020
- Certificate Installation , S/MIME, Client, and Document Signing
- client authentication , Client Certificate
Related Content
How to change your thales safenet/gemalto token password, enabling third-party signing certificates with esigner cloud signing, send a secure email using a s/mime certificate in the new outlook for mac, s/mime certificate management with microsoft azure active directory and intune using ssl.com azure integration tool, generate a certificate signing request in azure key vault, want to keep learning.
Subscribe to SSL.com’s newsletter, stay informed and secure.
All of SSL.com’s client authentication certificates and NAESB client certificates can be used for client authentication in web applications. Certificate-based client authentication is a great way for businesses to add an additional authentication factor for employees who are working from home . ClientAuth certificates can be used be used as part of a SSO (Single Sign On) initiative. With so many phishing scams out there, passwords alone are not enough to ensure good security!
This howto will show you how to use client certificates with the most popular desktop browsers. These instructions assume you have already downloaded and installed a PFX/PKCS12 file with your certificate and private key, or you have a hardware token with the certificate and private key inserted in the computer.
SSL.com certificates offering client authentication are available for as little as $20.00 per year for basic S/MIME email protection and ClientAuth. Our full-featured Business Identity certificates offer Organization Validation (OV) and trusted signatures for Adobe PDF, starting at $ 249.66 per year.
Google Chrome, Microsoft Edge, Internet Explorer, Apple Safari
Chrome, Edge, IE, and Safari are all configured to use client certificates and private keys provided by the OS . This includes PFX files imported into the OS certificate store, and certificates and private keys stored on smart cards (including SSL.com’s Business Identity certificates). So, if you’ve installed your PFX file or have your USB token inserted into the computer, you should already be good to go for client authentication with these popular desktop browsers.
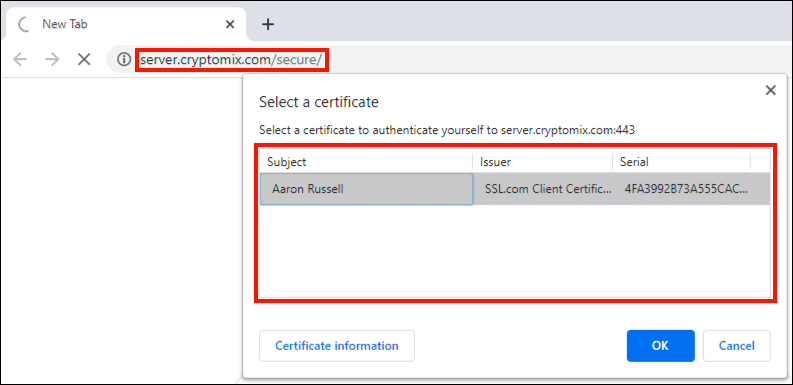
Confirm Installation
You can verify that installed client authentication certificates are available to your browser by navigating to https://server.cryptomix.com/secure/ . If certificates are present, a dialog box will appear, listing them.
Mozilla Firefox
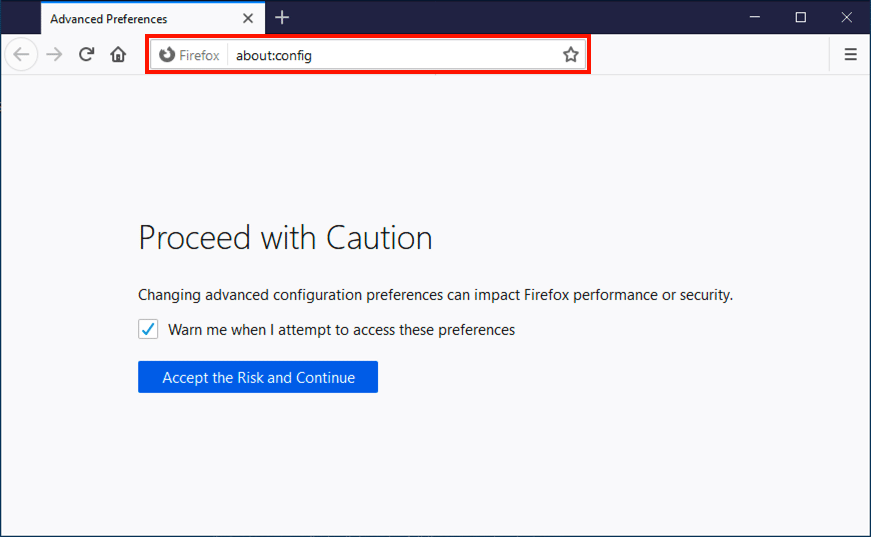
Use os certificate store (firefox 75 and later).
Beginning with version 75 , Firefox can be configured to use client certificates and private keys provided by the OS on Windows and macOS. This method supports both PFX files imported into the OS certificate store, and certificates and private keys stored on smart cards (including SSL.com’s Business Identity certificates). In general, this is now the preferred and simplest method to use client certificates in Firefox.
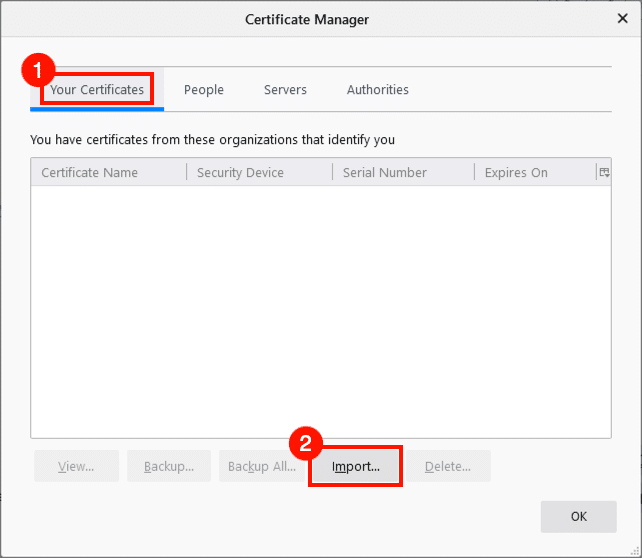
Install Client Certificates in Firefox
You can also install a certificate and private key directly into Firefox’s own certificate store by importing a PFX/PKCS12 file as described below. This method is not appropriate for certificates with non-exportable private keys stored on smart cards, including SSL.com’s Business Identity Email, ClientAuth, and Document Signing certificates.
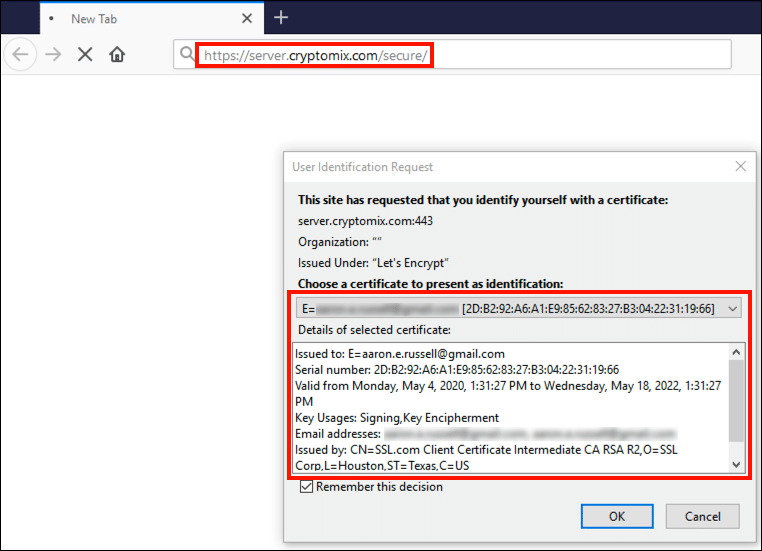
You can verify that installed client authentication certificates are available to Firefox by navigating to https://server.cryptomix.com/secure/ . If certificates are present, a dialog box will appear, listing them.
Stay Informed and Secure
SSL.com is a global leader in cybersecurity, PKI and digital certificates. Sign up to receive the latest industry news, tips, and product announcements from SSL.com .
We’d love your feedback
Take our survey and let us know your thoughts on your recent purchase.
- Privacy Overview
- 3rd Party Cookies
This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognizing you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
For more information read our Cookie and privacy statement .
This website uses Google Analytics & Statcounter to collect anonymous information such as the number of visitors to the site, and the most popular pages.
Keeping these cookies enabled helps us to improve our website.
Please enable Strictly Necessary Cookies first so that we can save your preferences!
Stack Exchange Network
Stack Exchange network consists of 183 Q&A communities including Stack Overflow , the largest, most trusted online community for developers to learn, share their knowledge, and build their careers.
Q&A for work
Connect and share knowledge within a single location that is structured and easy to search.
Import PKCS#12 Certificate into MacOS 13.4 for use with Safari as a client certificate
I want to import a client certificate into MacOS 13.4 for use with Safari.
I have imported the certificate both with Keychain access and the security command into MacOS.
Command used: security import Documents/ssl/nginx/client.pfx -P <passphrase> -k "/Users/ronnyforberger/Library/Keychains/login.keychain-db" -A
I still get 400 Bad Request
No required SSL certificate was sent
from the Webserver.
I have tried to set a new identity setting to the url of the website I want to reach with the client certificate, but still the same error message.
I have tried to both import the certificate to the login and system key chains, with no success.
I cannot import the certificate in the "local objects" keychain, I get an error that the keychain does not exist (though shown in the Keychain access).
So any ideas how to successfully import the client certificate into MacOS so that Safari uses it for the client connection for this specific website?
- certificate
- idk whether this applies to all certificates, as I only have ever needed one custom cert that I am issued every year - but I just double click it & it 'magically works'. I don't even extract it first from the email it arrives in, just double-click the icon right in the mail. – Tetsujin Commented Jun 23, 2023 at 10:44
- OK, well I can install the certificate, no problems here, but Safari or the whatever MacOS logic does not use it for the site as a client certificate. I had no problems with that on Windows and Linux with Chrome. – Ronny Forberger Commented Jun 24, 2023 at 13:09
- Have you checked that the Issuing/Root CA of the client certificate is also in your key chain? At least in some cases, MacOS does not import the CA certificate from the PFX file, while Windows does extract and import it. – Froggy Commented Dec 21, 2023 at 7:41
- If you used OpenSSL v3 to create the PKCS#12 file, you should check out this SO answer which explains that that version uses an algorithm that is not supported by macOS's security frameworks. – nickform Commented Dec 22, 2023 at 15:36
You must log in to answer this question.
Browse other questions tagged mac ssl certificate safari keychain ..
- The Overflow Blog
- Mobile Observability: monitoring performance through cracked screens, old...
- Featured on Meta
- Announcing a change to the data-dump process
- Bringing clarity to status tag usage on meta sites
Hot Network Questions
- Why is the !? annotation so rare?
- What did Horace say about combining Latin and Greek roots?
- If Starliner returns safely on autopilot, can this still prove that it's safe? Could it be launched back up to the ISS again to complete its mission?
- Is a company liable for "potential" harms?
- What is the relation between rope length, object weight and force needed?
- What is this device in my ceiling making out of battery chirps?
- Expensive constructors. Should they exist? Should they be replaced?
- Explain how π – 1 + 50 + ⅔ × 1000 is PLONK
- Identifications in differential geometry
- How to setup a home lab with a custom domain name?
- Is it illegal to use a fake state ID to enter a private establishment even when a legitimate ID would've been fine?
- Which version of Netscape, on which OS, appears in the movie “Cut” (2000)?
- Coding exercise to represent an integer as words using python
- What does ציר"ו stand for?
- Soldering RG179 coaxial cable directly to PCB
- Does an airplane fly less or more efficiently after an mid-flight engine failure?
- What is this 3 terminal white + grey surface mount device?
- Lore reasons for being faithless
- World Building Knowledgebase - How to write good Military World Building
- ESTA is not letting me pay
- Fast way to test if an argument is an integer in LaTeX3?
- Could an alien pathogen actually have an effect on us?
- Best way to explain the thinking steps from x^2 = 9 to x=±3
- A SF novel where one character makes a "light portrait" of another one, with huge consequences
- Return to GlobalSign
- GCC Account Login
- English / EN
GlobalSign Website in other countries/regions
- Português / PT
- Español / ES
- Francais / FR
GlobalSign Support
Install pfx / pkcs#12 file - mac osx for safari & chrome.
Feb 19, 2024
Install PFX / PKCS#12 File - MAC OSX for Safari & Chrome
Installing a PFX / PKCS#12 File in MAC OSX for Safari & Chrome Article Purpose: This article provides step-by-step instructions for installing a PKCS#12 file in MAC OS using Chrome. If this is not the solution you are looking for, please search for your solution in the search bar above. Note: This guide does not support Code Signing since it now requires a token as mandated in the Minimum Requirements for Code Signing .
- Enter the password.
- The certificate is now installed and can be used for network or secure web site client authentication.
- Enter the password and complete the process.
- The certificate is now installed and can be used for network or secure website client authentication.
Related Articles
Windows mobile pda - install personalsign certificate.
Sep 24, 2013, 10:28 AM
This article provides step-by-step instructions for installing your PersonalSign certificate in Windows Mobile PDA. If this is not the solution you are looking for, please search for your solution in the search bar above.

Installing Your PersonalSign Certificate - Microsoft Outlook 2007
Sep 25, 2019, 11:43 AM
This article provides step-by-step instructions for installing your certificate in Outlook 2007. If this is not the solution you are looking for, please search for your solution in the search bar above.
Add Timestamping - Microsoft Office 2010, 2013, 2016 & 2019
Jul 10, 2019, 1:01 PM
By default, when a digital signature is placed in Microsoft Office, the timestamp is based on the local computer's time.
GlobalSign System Alerts
View recent system alerts.
Atlas Discovery
Scan your endpoints to locate all of your Certificates.
SSL Configuration Test
Check your certificate installation for SSL issues and vulnerabilities.
Contact Support
Chat with us, submit a ticket.
- Contact Us Online
- Support Ticket
This page requires JavaScript.
Please turn on JavaScript in your browser and refresh the page to view its content.
- Announcements
- Axiad Cloud
- Axiad UCMS (on premises)
- Legal, Privacy, & Technical Documentation
- 11 May 2023
- 1 Minute to read
MacOS PKI Integration with Safari
- Updated on 11 May 2023
If a server requests a certificate for authentication, Safari automatically prompts you for which certificate to present. Safari’s client certificates and related preferences are stored in Keychain Manager. When you select a certificate to use with a web site, it stores an entry in the Keychain Manager with a kind of identity preference.
- Customize Your Certificate Entries
- In the Finder, navigate to Applications > Utilities > Keychain Access .
- Click My Certificates .
- Right-click the certificate and select New Identity Preference .
- In the pop-up window, modify the URL (you can use wildcards in this field).
- Click Add . The certificate entry is updated.
- Locate Certificate and Identity Preferences Entries
- Select All Items .
- Search for the partial URL and/or certificate name as appropriate. The certificate name or URL displays in the results list.
What's Next
- Mail App for MacOS: Signing & Encrypting Email
Table of contents
- © 2023 Axiad IDS, Inc.
- Privacy Policy
- Social Responsibility Policy
Apple Platform Deployment
- Intro to Apple platform deployment
- Intro to declarative device management
- Use declarative device management to manage Apple devices
- Intro to MDM profiles
- Intro to MDM payloads
- About device supervision
- Choose a deployment model
- Intro to Apple device enrollment types
- User Enrollment and MDM
- Device Enrollment and MDM
- Automated Device Enrollment and MDM
- Deploy Apple TV
- Deploy Apple Watch
- Deploy Apple Vision Pro
- Shared iPad overview
- Prepare Shared iPad
- Choose an MDM solution
- Intro to planning your MDM migration
- Configure your new MDM solution
- Reenroll devices in MDM
- Back up and restore devices
- Use standards-based services
- Deploy devices using Apple School Manager, Apple Business Manager, or Apple Business Essentials
- Configure devices
- Install apps with Apple Configurator
- Add Apple devices to Apple School Manager, Apple Business Manager, or Apple Business Essentials
- Configure your network for MDM
- Configure devices to work with APNs
- Prepare to use eSIMs with Apple devices
- Use MDM to deploy devices with cellular connections
- Support for private 5G and LTE networks
- Optimize your Wi-Fi networks
- Review aggregate throughput for Wi-Fi networks
- Intro to content caching
- Set up content caching
- Use DNS TXT records
- Advanced content caching settings
- Content caching from the command line
- Content caching metrics
- Set up a shared internet connection
- Intro to Apple identity services
- Platform SSO for macOS
- Enrollment SSO for iPhone and iPad
- Managed Apple IDs
- Service access with Managed Apple IDs
- iMessage and FaceTime
- Intro to single sign-on
- Kerberos SSO extension
- Integrate with Microsoft Entra ID
- Integrate with Microsoft Exchange
- Identify an iPhone, iPad, or Apple Vision Pro using Microsoft Exchange
- Integrate Mac computers with Active Directory
- Manage Setup Assistant
- Configure Setup Assistant panes in Apple TV
- Set up local macOS accounts
- Plan your configuration profiles
- Review MDM payloads
- Review MDM restrictions
- Review declarative configurations
- About software updates
- Software update process
- Installing and enforcing software updates
- Use MDM to deploy software updates
- Intro to content distribution
- Content distribution methods
- Distribute Managed Apps
- Distribute Custom Apps
- Distribute Unlisted Apps
- Distribute proprietary in-house apps
- Distribute custom packages for Mac
- Bundle IDs for native iPhone and iPad apps
- Bundle IDs for native Apple TV apps
- Manage login items and background tasks on Mac
- How Apple devices join Wi-Fi networks
- Connect to 802.1X networks
- Wi-Fi roaming support
- Cisco network enhancements
- Wi-Fi specifications for Apple devices
- VPN overview
- Cisco IPsec VPN setup
- Use a VPN proxy and certificate configuration
- Use network relays
- Filter content
- Use AirPlay
- Intro to device management security
- Rapid Security Responses
- Lock and locate devices
- Erase devices
- Activation Lock
- Manage accessory access
- Enforce password policies
- Use persistent tokens
- Use built-in network security features
- Managed Device Attestation
- Intro to certificate management
- Distribute certificates
- Intro to smart card integration
- Supported smart card functions on iPhone and iPad
- Use a smart card on iPhone and iPad
- Supported smart card functions on Mac
- Use a smart card on Mac
- Configure a Mac for smart card–only authentication
- FileVault and smart card usage
- Advanced smart card options
- Startup security
- System and kernel extensions in macOS
- Intro to FileVault
- Use secure and bootstrap tokens
- Manage FileVault with MDM
- Mac app security enhancements
- User Enrollment MDM information
- Device Enrollment MDM payload list
- Automated Device Enrollment MDM payload list
- Payload list for iPhone and iPad
- Payload list for Mac
- Payload list for Apple TV
- Payload list for Apple Watch
- Payload list for Apple Vision Pro
- Payload list for Shared iPad
- Restrictions for iPhone and iPad
- Restrictions for Mac
- Restrictions for Apple TV
- Restrictions for Apple Watch
- Restrictions for Apple Vision Pro
- Restrictions for supervised devices
- MDM command list
- MDM settings command options list
- Device information queries
- Device network information queries
- Operating system queries
- Installed app queries
- Security queries
- Declarative status reports
- Accessibility payload settings
- Active Directory Certificate payload settings
- AirPlay payload settings
- AirPlay Security payload settings
- AirPrint payload settings
- App Lock payload settings
- Associated Domains payload settings
- Automated Certificate Management Environment (ACME) payload settings
- Autonomous Single App Mode payload settings
- Calendar payload settings
- Cellular payload settings
- Cellular Private Network payload settings
- Certificate Preference payload settings
- Certificate Revocation payload settings
- Certificate Transparency payload settings
- Certificates payload settings
- Conference Room Display payload settings
- Contacts payload settings
- Content Caching payload settings
- Directory Service payload settings
- DNS Proxy payload settings
- DNS Settings payload settings
- Dock payload settings
- Domains payload settings
- Energy Saver payload settings
- Exchange ActiveSync (EAS) payload settings
- Exchange Web Services (EWS) payload settings
- Extensible Single Sign-on payload settings
- Extensible Single Sign-on Kerberos payload settings
- Extensions payload settings
- FileVault payload settings
- Finder payload settings
- Firewall payload settings
- Fonts payload settings
- Global HTTP Proxy payload settings
- Google Accounts payload settings
- Home Screen Layout payload settings
- Identification payload settings
- Identity Preference payload settings
- Kernel Extension Policy payload settings
- LDAP payload settings
- Lights Out Management payload settings
- Lock Screen Message payload settings
- Login Window payload settings
- Managed Login Items payload settings
- Mail payload settings
- Wi-Fi settings
- Ethernet settings
- WEP, WPA, WPA2, WPA2/WPA3 settings
- Dynamic WEP, WPA Enterprise, and WPA2 Enterprise settings
- EAP settings
- HotSpot 2.0 settings
- Legacy Hotspot settings
- Cisco Fastlane settings
- Network Proxy Configuration settings
- Network Usage Rules payload settings
- Notifications payload settings
- Parental Controls payload settings
- Passcode payload settings
- Printing payload settings
- Privacy Preferences Policy Control payload settings
- Relay payload settings
- SCEP payload settings
- Security payload settings
- Setup Assistant payload settings
- Single Sign-on payload settings
- Smart Card payload settings
- Subscribed Calendars payload settings
- System Extensions payload settings
- System Migration payload settings
- Time Machine payload settings
- TV Remote payload settings
- VPN settings overview
- AppLayerVPN payload settings
- IKEv2 settings
- IPsec settings
- L2TP settings
- VPN Proxy settings
- Web Clips payload settings
- Web Content Filter payload settings
- Xsan payload settings
- Declarative app configuration settings
- Authentication credentials and identity asset settings
- Calendar declarative settings
- Certificates declarative configuration
- Contacts declarative configuration
- Exchange declarative configuration
- Google Accounts declarative configuration
- LDAP declarative configuration
- Legacy interactive profile declarative configuration
- Legacy profile declarative configuration
- Mail declarative configuration
- Passcode declarative configuration
- Passkey Attestation declarative configuration
- Screen Sharing declarative configuration
- Service configuration files declarative configuration
- Software Update declarative configuration
- Subscribed Calendars declarative configuration
- Join AppleSeed for IT
- AppleCare support
- Professional services
- Deployment and management training
- Apple Consultants Network
- Apple web resources
- Document revision history
Distribute certificates to Apple devices
You can manually distribute certificates to iPhone, iPad, and Apple Vision Pro devices. When users receive a certificate, they tap to review the contents, then tap to add the certificate to the device. When an identity certificate is installed, users are asked for the password that protects it. If a certificate’s authenticity can’t be verified, it’s shown as untrusted, and the user can decide whether to add it to the device.
You can manually distribute certificates to Mac computers. When users receive a certificate, they double-click it to open Keychain Access and review the contents. If the certificate matches expectations, users select the desired keychain and click the Add button. Most user certificates need to be installed in the login keychain. When an identity certificate is installed, users are asked for the password that protects it. If a certificate’s authenticity can’t be verified, it’s shown as untrusted, and the user can decide whether to add it to the Mac.
Some certificate identities can be automatically renewed on Mac computers. For more information, see the Apple Support article Automatically renew certificates delivered via a configuration profile .
Certificate deployment methods using MDM payloads
The following table shows the different payloads for deploying certificates using configuration profiles. These include the Active Directory Certificate payload, the Certificate payload (for a PKCS #12 identity certificate), the Automated Certificate Management Environment (ACME) payload, and the Simple Certificate Enrollment Protocol (SCEP) payload.
To associate services with a particular identity, configure an ACME, SCEP, or certificate payload, and then configure the desired service in the same configuration profile. For example, an SCEP payload can be configured to provision an identity for the device, and in the same configuration profile, a Wi-Fi payload can be configured for WPA2 Enterprise/EAP-TLS using the device certificate resulting from the SCEP enrollment for authentication.
To associate services with a particular identity in macOS, configure an Active Directory Certificate, ACME, SCEP, or certificate payload, then configure the desired service in the same configuration profile. For example, you can configure an Active Directory Certificate payload to provision an identity for the device, and in the same configuration profile, a Wi-Fi payload can be configured for WPA2 Enterprise EAP-TLS using the device certificate that results from the Active Directory Certificate enrollment for authentication.
Renew certificates installed by configuration profiles
To ensure ongoing service access, certificates deployed using an MDM solution should be renewed before they expire. To do so, MDM solutions can query the installed certificates, inspect the expiration date, and issue a new profile or configuration ahead of time.
For Active Directory certificates, when the certificate identities are deployed as part of a device profile, the default behavior is automatic renewal in macOS 13 or later. Administrators can set a system preference to modify this behavior. For more information see the Apple Support article Automatically renew certificates delivered via a configuration profile .
Install certificates using Mail or Safari
You can send a certificate as an attachment to a mail message or host a certificate on a secure website where users download the certificate on their Apple devices.
Remove and revoke certificates
An MDM solution can view all certificates on a device and remove any certificates it has installed.
Additionally, the Online Certificate Status Protocol (OCSP) is supported to check the status of certificates. When an OCSP-enabled certificate is used, iOS, iPadOS, macOS, and visionOS periodically validate it to make sure it hasn’t been revoked.
To revoke certificates using a configuration profile, see Certificate Revocation MDM payload settings .
To manually remove an installed certificate in iOS, iPadOS, and visionOS 1.1 or later, go to Settings > General > Device Management, select a profile, tap More Details, then tap the certificate to remove it. If you remove a certificate that’s required for accessing an account or network, the iPhone, iPad, or Apple Vision Pro can no longer connect to those services.
To manually remove an installed certificate in macOS, launch the Keychain Access app, then search for the certificate. Select it, then delete it from the keychain. If you remove a certificate that’s required for accessing an account or network, the Mac can no longer connect to those services.
You can make a difference in the Apple Support Community!
When you sign up with your Apple ID , you can provide valuable feedback to other community members by upvoting helpful replies and User Tips .
Looks like no one’s replied in a while. To start the conversation again, simply ask a new question.
certificate is not standards compliant
I am trying to launch a training courses and getting the below certificate error. I am using the below version. Can you please let me know the reason
Mac OS Monterey Version 12.3
Safari Version 15.4 (17613.1.17.1.6)
Posted on Apr 19, 2023 10:07 AM
Similar questions
- certificate i am using MacBook for business purpose so my problem is i install one certificate name is western union is base on Microsoft so problem is this no working showing error "you cant open the application "wupos_service_x86.exe" because Microsoft windows applications are not supported on os X. 441 1
- How do I correct websites' "certificate is not standards compliant"? I'm using Apple safari Monterary 15.3 and 15.4 version for many websites, I visit using Safari are giving me the "This Connection is Not Private" message. When I click "Show Details" then "view the certificate" I get a window saying the website's "certificate is not standards compliant Meanwhile this websites are working on other browsers and updated safari browser Regards, Nikhil 601 2
- Error Code: -26276 I downloaded (with no issue on my MacBook Pro Early 2015, running macOS Monterey 12.5.1 (21G83)) the FCPCAG2toEntrustManagedServicesRootCA20201118 certificate and am unable to import it to keychain access as I get the error message: An error occurred. Unable to import the certificate. Error: -26276 Please advise how to fix that. Thx 1362 1
Loading page content
Page content loaded
May 24, 2024 5:46 PM in response to tomasfromcardiff
It's almost certainly about the lifetime of the cert. Chances are this certificate was issued for a period longer than 397 days. It's a really misleading error, because there's no "standard" that is in play here, it's an arbitrary apple decision.
According to a document published in August of 2023
About upcoming limits on trusted certificates - Apple Support
And then, in November 2023, they changed this tune, making the requirement 825 days maximum for ALL certs issued after July 1, 2019 (regardless of if it had a private trust anchor or not).
Requirements for trusted certificates in iOS 13 and macOS 10.15 - Apple Support
Apr 20, 2023 2:42 AM in response to John Galt
We checked with AWS and below is their feedback
As the same certificate seems to work perfectly fine with other browsers and latest safari version, this doesn't seems to be a certificate issue. This seems to be case of client-side MacOS error.
When I access the same training on other versions line Big Sur and Ventura and the issue was not seen.
Can you please advise
Apr 20, 2023 7:11 AM in response to John Galt
I tried that and we also deleted the cache, yet getting the same error.
I was trying on Big Sur and Ventura with Safari on another machine and did not see this error. The training is working seamlessly on Big Sur and Ventura with Safari.
If it were a AWS issue then this certificate error would happen on Big Sur and Ventura with Safari? why is only happening with the below combination:
Hardware: 2.6 GHz 6-Core Intel Core i7
Can you please advise?
Apr 20, 2023 4:37 PM in response to gaurang176
What is your MacBook Pro's model identifier? An example might be MacBookPro11,3 .
To determine that information please read Identify your MacBook Pro model - Apple Support .
Apr 19, 2023 3:44 PM in response to gaurang176
Presumably the course content is hosted on Amazon's servers. The certificate was issued by them, and it is not valid.
Apr 20, 2023 3:43 AM in response to gaurang176
Since the certificate is not valid, delete it. Reloading the web page should cause AWS to issue a new one.
Apr 25, 2023 1:06 AM in response to John Galt
I am seeing the issue on below devices:
MacBookPro15,1, MacBookPro15,3
Jun 21, 2023 10:14 AM in response to gaurang176
did anyone solve this?

IMAGES
VIDEO
COMMENTS
Using client certificates with Safari present a number of problems: Safari asks to select a client certificate on each page of the site (annoying) Safari might even re-ask you to choose a certific...
A certificate, also known as a "digital certificate" or a "public key certificate," is a file that helps keep web communications secure. Certificates are issued by trusted organizations, such as VeriSign, Inc. or RSA Security, Inc. When you visit an encrypted website—for example, to do online banking—Safari checks if the site's ...
Make Safari accept an untrusted certificate I'm using Safari 10.0.1 on macOS Sierra 10.12.1 I'm trying to view use Safari to view a web server I use for staging content. Since it's only a staging server, I have a certificate with an untrusted root (it's from the letsencrypt staging environment).
In Keychain Access on your Mac, you can add certificates to your keychain for quick access to secure websites and other resources.
Using certificates with Apple devices Apple devices include a number of preinstalled root certificates from various Certification Authorities (CAs), and iOS, iPadOS, macOS, and visionOS validate the trust for these root certificates. These digital certificates can be used to securely identify a client or server, and to encrypt the communication between them using the public and private key ...
This how-to will show you how to make sure that Chrome, Edge, IE, Firefox, and Safari are configured to use client authentication certificates.
I want to import a client certificate into MacOS 13.4 for use with Safari. I have imported the certificate both with Keychain access and the security command into MacOS. Command used: security import
Using safari on OS X 10.8.2 to connect to an internal server via https:, safari indicates a client certificate is required. Tried dragging the certificate from the url field to the desktop and add...
How to clear Safari SSL client certificate cache? I have two SSL client certificates which I can use to access an Apache web server via Safari. Let's call them Cert-A and Cert-B. I can use either certificate to authenticate. When I first accessed the web server, a selection dialog popped up and I chose Cert-A for authentication.
Installing a PFX / PKCS#12 File in MAC OSX for Safari & Chrome Article Purpose: This article provides step-by-step instructions for installing a PKCS#12 file in MAC OS using Chrome.
X509 Login Keeps Prompting in Safari When trying to login to a site protected by a client certificate login in Safari 12.1.1, it keeps prompting for the certificate to use from the keychain even though have provided it before. This use to work with the certificate but now is not providing the certificate to the site.
If you receive a certificate, perhaps from a .cer file, as shown in Storing a DER-Encoded X.509 Certificate, you can store it in your keychain for safekeeping. As with other keychain operations, begin by creating a query: In addition to including the certificate reference itself and the kSecClassCertificate attribute value, you add a label with ...
In the Keychain Access app on your Mac, select a keychain from one of the keychains lists, then double-click a certificate. Next to Trust, click the arrow to display the trust policies for the certificate. To override the trust policies, choose new trust settings from the pop-up menus.
If a server requests a certificate for authentication, Safari automatically prompts you for which certificate to present. Safari's client certificates and related preferences are stored in Keychain Manager. When you select a certificate to use with a web site, it stores an entry in the Keychain Manager with a kind of identity preference.
Learn how to inspect a certificate file without installing it on your Mac, using the openssl command or other tools.
Safari (or any other web client) doesn't present its client certificate unless requested by the website. So your client certificate is safe. The server is always the one asking for the certificate, sending along its own certificate. Therefore, your browser will see that the certificate do not match the one you have and will result in failure ...
Safari keeps asking for client certificates Hello, I'm facing the following issue: When trying to access certain websites a pop-up in Safari appears asking for a client-certificate and providing a list of local client-certificates from which to choose one.
You can manually distribute certificates to Apple devices. When users receive a certificate, they review the contents, then add the certificate to the device.
Safari Version Affected: 13.0.x and newer. Description: Client-side certificates used for validating users through IIS may not work with the latest versions of MacOS and Safari. This means that any web browser login requiring the user to present a certificate as part of their authentication may potentially have issues.
Safari and client certificates for authentication issues Hitting an issue in Safari where I have troubles to make a client certificate associated to a web site where no certificates was asked when visiting the web site.
Since installing Safari 14, I can't find a way of trusting an invalid SSL certificate (either expired or set up for the wrong hostname). I used to be able to click on the address bar and then trust...
In Safari: Click the padlock icon in the URL bar. Click the Show Certificate button in the dialog that appears. Click on the certificate icon, and drag it to a Finder window (or the Desktop) In Google Chrome: Click the padlock icon in the URL bar. If the dialog that appears has a "Connection is secure" line, click on that.
As the same certificate seems to work perfectly fine with other browsers and latest safari version, this doesn't seems to be a certificate issue. This seems to be case of client-side MacOS error.