
- Business, Finance & Law
- Managers' Guides to Computing

Your Amazon Prime 30-day FREE trial includes:
Unlimited Premium Delivery is available to Amazon Prime members. To join, select "Yes, I want a free trial with FREE Premium Delivery on this order." above the Add to Basket button and confirm your Amazon Prime free trial sign-up.
Important: Your credit card will NOT be charged when you start your free trial or if you cancel during the trial period. If you're happy with Amazon Prime, do nothing. At the end of the free trial, you will be charged £95/year for Prime (annual) membership or £8.99/month for Prime (monthly) membership.
Buy new: .savingPriceOverride { color:#CC0C39!important; font-weight: 300!important; } .reinventMobileHeaderPrice { font-weight: 400; } #apex_offerDisplay_mobile_feature_div .reinventPriceSavingsPercentageMargin, #apex_offerDisplay_mobile_feature_div .reinventPricePriceToPayMargin { margin-right: 4px; } -6% £42.25 £ 42 . 25 FREE delivery Thursday, 13 June Dispatches from: Amazon Sold by: Amazon
Return this item for free.
Free returns are available for the shipping address you chose. For a full refund with no deduction for return shipping, you can return the item for any reason in new and unused condition.
- Go to your orders and start the return
- Select the return method
Save with Used - Like New .savingPriceOverride { color:#CC0C39!important; font-weight: 300!important; } .reinventMobileHeaderPrice { font-weight: 400; } #apex_offerDisplay_mobile_feature_div .reinventPriceSavingsPercentageMargin, #apex_offerDisplay_mobile_feature_div .reinventPricePriceToPayMargin { margin-right: 4px; } £35.84 £ 35 . 84 £2.80 delivery 13 - 15 June Dispatches from: World of Books Ltd Sold by: World of Books Ltd

Download the free Kindle app and start reading Kindle books instantly on your smartphone, tablet or computer – no Kindle device required .
Read instantly on your browser with Kindle for Web.
Using your mobile phone camera - scan the code below and download the Kindle app.

Image Unavailable

- To view this video download Flash Player
Follow the author

Zero Trust Journey Across the Digital Estate Paperback – 1 Sept. 2022
Purchase options and add-ons.
"Zero Trust is the strategy that organizations need to implement to stay ahead of cyber threats, period. The industry has 30 plus years of categorical failure that shows us that our past approaches, while earnest in their efforts, have not stopped attackers. Zero Trust strategically focuses on and systematically removes the power and initiatives hackers and adversaries need to win as they circumvent security controls. This book will help you and your organization have a better understanding of what Zero Trust really is, recognize its history, and gain prescriptive knowledge that will help you and your enterprise finally begin beating the adversaries in the chess match that is cyber security strategy."
Dr. Chase Cunningham (aka Dr. Zero Trust), Cyberware Expert
Today’s organizations require a new security approach that effectively adapts to the challenges of the modern environment, embraces the mobile workforce, and protects people, devices, apps, and data wherever they are located. Zero Trust is increasingly becoming the critical security approach of choice for many enterprises and governments; however, security leaders often struggle with the significant shifts in strategy and architecture required to holistically implement Zero Trust.
This book seeks to provide an end-to-end view of the Zero Trust approach across organizations’ digital estates that includes strategy, business imperatives, architecture, solutions, human elements, and implementation approaches that could significantly enhance these organizations' success in learning, adapting, and implementing Zero Trust. The book concludes with a discussion of the future of Zero Trust in areas such as artificial intelligence, blockchain technology, operational technology (OT), and governance, risk, and compliance.
The book is ideal for business decision makers, cybersecurity leaders, security technical professionals, and organizational change agents who want to modernize their digital estate with the Zero Trust approach.
- ISBN-10 1032125497
- ISBN-13 978-1032125497
- Edition 1st
- Publication date 1 Sept. 2022
- Language English
- Dimensions 15.6 x 1.27 x 23.39 cm
- Print length 236 pages
- See all details
Product description
About the author, product details.
- Publisher : CRC Press; 1st edition (1 Sept. 2022)
- Language : English
- Paperback : 236 pages
- ISBN-10 : 1032125497
- ISBN-13 : 978-1032125497
- Dimensions : 15.6 x 1.27 x 23.39 cm
- Best Sellers Rank: 1,941,350 in Books ( See Top 100 in Books )
About the author
Abbas kudrati.
Abbas Kudrati is a highly regarded cybersecurity expert and accomplished public speaker, currently serving as Microsoft Asia's Lead Chief Cybersecurity Advisor for the Security Solutions Area. In this role, he advises on cutting-edge cybersecurity strategies and technologies to ensure Microsoft's clients remain safe in an increasingly digital world.
Beyond his work at Microsoft, Abbas is a sought-after executive advisor to numerous prestigious organizations, including LaTrobe University, HITRUST ASIA, and EC Council ASIA. He also supports the broader security community through his work with ISACA Chapters and by mentoring students.
As a bestselling author, Abbas has written several authoritative books on cybersecurity, including "Threat Hunting in the Cloud" by Wiley, "Zero Trust and Journey Across the Digital Estate" by CRC Press, and "Managing Risks in Digital Transformation" by Packt. He is also the Technical Editor for two books, "Effective Crisis Management" by BPB and "IoT Security with Microsoft Defender for IoT" by Packt.
Abbas is also a highly respected part-time Professor of Practice at LaTrobe University and a keynote speaker on a range of cybersecurity-related topics, including Zero-Trust, Cloud Security, Governance, Risk, and Compliance. His extensive expertise in the field of cybersecurity and engaging speaking style make him a popular choice for events, conferences, and corporate training sessions.
His post-nominals include C|CISO, CISM, CISA, CDPSE, CGEIT, CSX-P, Cobit5, Forrester ZTS, MS900, SCI900, AZ900, MCSE, MCSA, CCNA, CEH, CHFI, ECRP, CCSK, ITIL(F), Prince2 Practitioner, ISO 27001 L.A.
https://www.linkedin.com/in/akudrati/
Customer reviews
Customer Reviews, including Product Star Ratings, help customers to learn more about the product and decide whether it is the right product for them.
To calculate the overall star rating and percentage breakdown by star, we don’t use a simple average. Instead, our system considers things like how recent a review is and if the reviewer bought the item on Amazon. It also analyses reviews to verify trustworthiness.
- Sort reviews by Top reviews Most recent Top reviews
Top review from United Kingdom
There was a problem filtering reviews right now. please try again later..
Top reviews from other countries
- UK Modern Slavery Statement
- Sustainability
- Amazon Science
- Sell on Amazon
- Sell on Amazon Business
- Sell on Amazon Handmade
- Sell on Amazon Launchpad
- Supply to Amazon
- Protect and build your brand
- Associates Programme
- Fulfilment by Amazon
- Seller Fulfilled Prime
- Advertise Your Products
- Independently Publish with Us
- Host an Amazon Hub
- › See More Make Money with Us
- Instalments by Barclays
- Amazon Platinum Mastercard
- Amazon Classic Mastercard
- Amazon Currency Converter
- Payment Methods Help
- Shop with Points
- Top Up Your Account
- Top Up Your Account in Store
- COVID-19 and Amazon
- Track Packages or View Orders
- Delivery Rates & Policies
- Amazon Prime
- Returns & Replacements
- Manage Your Content and Devices
- Recalls and Product Safety Alerts
- Amazon Mobile App
- Customer Service
- Accessibility
- Conditions of Use & Sale
- Privacy Notice
- Cookies Notice
- Interest-Based Ads Notice
- Find a Library
- Browse Collections
- Zero Trust Journey Across the Digital Estate
By Abbas Kudrati

Add Book To Favorites
Is this your library?
Sign up to save your library.
With an OverDrive account, you can save your favorite libraries for at-a-glance information about availability. Find out more about OverDrive accounts.
9781032125480
Abbas Kudrati
01 September 2022
Find this title in Libby, the library reading app by OverDrive.

Search for a digital library with this title
Title found at these libraries:.
"Zero Trust is the strategy that organizations need to implement to stay ahead of cyber threats, period. The industry has 30 plus years of categorical failure that shows us that our past approaches, while earnest in their efforts, have not stopped attackers. Zero Trust strategically focuses on and systematically removes the power and initiatives hackers and adversaries need to win as they circumvent security controls. This book will help you and your organization have a better understanding of what Zero Trust really is, recognize its history, and gain prescriptive knowledge that will help you and your enterprise finally begin beating the adversaries in the chess match that is cyber security strategy."
Dr. Chase Cunningham (aka Dr. Zero Trust), Cyberware Expert
Today's organizations require a new security approach that effectively adapts to the challenges of the modern environment, embraces the mobile workforce, and protects people, devices, apps, and data wherever they are located. Zero Trust is increasingly becoming the critical security approach of choice for many enterprises and governments; however, security leaders often struggle with the significant shifts in strategy and architecture required to holistically implement Zero Trust.
This book seeks to provide an end-to-end view of the Zero Trust approach across organizations' digital estates that includes strategy, business imperatives, architecture, solutions, human elements, and implementation approaches that could significantly enhance these organizations' success in learning, adapting, and implementing Zero Trust. The book concludes with a discussion of the future of Zero Trust in areas such as artificial intelligence, blockchain technology, operational technology (OT), and governance, risk, and compliance.
The book is ideal for business decision makers, cybersecurity leaders, security technical professionals, and organizational change agents who want to modernize their digital estate with the Zero Trust approach.

- Computers & Technology
- Programming
Enjoy Prime FREE for 30 days
Here's what Amazon Prime has to offer:

Download the free Kindle app and start reading Kindle books instantly on your smartphone, tablet or computer – no Kindle device required .
Read instantly on your browser with Kindle for Web.
Using your mobile phone camera, scan the code below and download the Kindle app.

Image Unavailable

- To view this video, download Flash Player
Follow the author

Zero Trust Journey Across the Digital Estate Paperback – Sept. 1 2022
Purchase options and add-ons.
"Zero Trust is the strategy that organizations need to implement to stay ahead of cyber threats, period. The industry has 30 plus years of categorical failure that shows us that our past approaches, while earnest in their efforts, have not stopped attackers. Zero Trust strategically focuses on and systematically removes the power and initiatives hackers and adversaries need to win as they circumvent security controls. This book will help you and your organization have a better understanding of what Zero Trust really is, recognize its history, and gain prescriptive knowledge that will help you and your enterprise finally begin beating the adversaries in the chess match that is cyber security strategy."
Dr. Chase Cunningham (aka Dr. Zero Trust), Cyberware Expert
Today’s organizations require a new security approach that effectively adapts to the challenges of the modern environment, embraces the mobile workforce, and protects people, devices, apps, and data wherever they are located. Zero Trust is increasingly becoming the critical security approach of choice for many enterprises and governments; however, security leaders often struggle with the significant shifts in strategy and architecture required to holistically implement Zero Trust.
This book seeks to provide an end-to-end view of the Zero Trust approach across organizations’ digital estates that includes strategy, business imperatives, architecture, solutions, human elements, and implementation approaches that could significantly enhance these organizations' success in learning, adapting, and implementing Zero Trust. The book concludes with a discussion of the future of Zero Trust in areas such as artificial intelligence, blockchain technology, operational technology (OT), and governance, risk, and compliance.
The book is ideal for business decision makers, cybersecurity leaders, security technical professionals, and organizational change agents who want to modernize their digital estate with the Zero Trust approach.
- ISBN-10 1032125497
- ISBN-13 978-1032125497
- Edition 1st
- Publication date Sept. 1 2022
- Language English
- Dimensions 15.6 x 1.27 x 23.39 cm
- Print length 212 pages
- See all details
Frequently bought together

Customers who bought this item also bought

Product description
About the author, product details.
- Publisher : CRC Press; 1st edition (Sept. 1 2022)
- Language : English
- Paperback : 212 pages
- ISBN-10 : 1032125497
- ISBN-13 : 978-1032125497
- Item weight : 1.04 kg
- Dimensions : 15.6 x 1.27 x 23.39 cm
- #551 in Computer Security
- #977 in Computer Cryptography
- #992 in Cryptography Algorithms
About the author
Abbas kudrati.
Abbas Kudrati is a highly regarded cybersecurity expert and accomplished public speaker, currently serving as Microsoft Asia's Lead Chief Cybersecurity Advisor for the Security Solutions Area. In this role, he advises on cutting-edge cybersecurity strategies and technologies to ensure Microsoft's clients remain safe in an increasingly digital world.
Beyond his work at Microsoft, Abbas is a sought-after executive advisor to numerous prestigious organizations, including LaTrobe University, HITRUST ASIA, and EC Council ASIA. He also supports the broader security community through his work with ISACA Chapters and by mentoring students.
As a bestselling author, Abbas has written several authoritative books on cybersecurity, including "Threat Hunting in the Cloud" by Wiley, "Zero Trust and Journey Across the Digital Estate" by CRC Press, and "Managing Risks in Digital Transformation" by Packt. He is also the Technical Editor for two books, "Effective Crisis Management" by BPB and "IoT Security with Microsoft Defender for IoT" by Packt.
Abbas is also a highly respected part-time Professor of Practice at LaTrobe University and a keynote speaker on a range of cybersecurity-related topics, including Zero-Trust, Cloud Security, Governance, Risk, and Compliance. His extensive expertise in the field of cybersecurity and engaging speaking style make him a popular choice for events, conferences, and corporate training sessions.
His post-nominals include C|CISO, CISM, CISA, CDPSE, CGEIT, CSX-P, Cobit5, Forrester ZTS, MS900, SCI900, AZ900, MCSE, MCSA, CCNA, CEH, CHFI, ECRP, CCSK, ITIL(F), Prince2 Practitioner, ISO 27001 L.A.
https://www.linkedin.com/in/akudrati/
Customer reviews
- Sort reviews by Top reviews Most recent Top reviews
Top reviews from Canada
Top reviews from other countries.
- Amazon and Our Planet
- Modern Slavery Statement
- Investor Relations
- Press Releases
- Amazon Science
- Sell on Amazon
- Supply to Amazon
- Become an Affiliate
- Protect & Build Your Brand
- Sell on Amazon Handmade
- Advertise Your Products
- Independently Publish with Us
- Host an Amazon Hub
- Amazon.ca Rewards Mastercard
- Shop with Points
- Reload Your Balance
- Amazon Currency Converter
- Amazon Cash
- Shipping Rates & Policies
- Amazon Prime
- Returns Are Easy
- Manage your Content and Devices
- Recalls and Product Safety Alerts
- Customer Service
- Conditions of Use
- Privacy Notice
- Interest-Based Ads
- Amazon.com.ca ULC | 40 King Street W 47th Floor, Toronto, Ontario, Canada, M5H 3Y2 |1-877-586-3230

- Kindle Store
- Kindle eBooks
Promotions apply when you purchase
These promotions will be applied to this item:
Some promotions may be combined; others are not eligible to be combined with other offers. For details, please see the Terms & Conditions associated with these promotions.
Buy for others
Buying and sending kindle ebooks to others.
- Select quantity
- Buy and send Kindle eBooks
- Recipients can read on any device
These ebooks can only be redeemed by recipients in the India. Redemption links and eBooks cannot be resold.

Download the free Kindle app and start reading Kindle books instantly on your smartphone, tablet or computer – no Kindle device required .
Read instantly on your browser with Kindle for Web.
Using your mobile phone camera, scan the code below and download the Kindle app.

Image Unavailable

- To view this video download Flash Player
Follow the author

Zero Trust Journey Across the Digital Estate 1st Edition, Kindle Edition
"Zero Trust is the strategy that organizations need to implement to stay ahead of cyber threats, period. The industry has 30 plus years of categorical failure that shows us that our past approaches, while earnest in their efforts, have not stopped attackers. Zero Trust strategically focuses on and systematically removes the power and initiatives hackers and adversaries need to win as they circumvent security controls. This book will help you and your organization have a better understanding of what Zero Trust really is, recognize its history, and gain prescriptive knowledge that will help you and your enterprise finally begin beating the adversaries in the chess match that is cyber security strategy."
Dr. Chase Cunningham (aka Dr. Zero Trust), Cyberware Expert
Today’s organizations require a new security approach that effectively adapts to the challenges of the modern environment, embraces the mobile workforce, and protects people, devices, apps, and data wherever they are located. Zero Trust is increasingly becoming the critical security approach of choice for many enterprises and governments; however, security leaders often struggle with the significant shifts in strategy and architecture required to holistically implement Zero Trust.
This book seeks to provide an end-to-end view of the Zero Trust approach across organizations’ digital estates that includes strategy, business imperatives, architecture, solutions, human elements, and implementation approaches that could significantly enhance these organizations' success in learning, adapting, and implementing Zero Trust. The book concludes with a discussion of the future of Zero Trust in areas such as artificial intelligence, blockchain technology, operational technology (OT), and governance, risk, and compliance.
The book is ideal for business decision makers, cybersecurity leaders, security technical professionals, and organizational change agents who want to modernize their digital estate with the Zero Trust approach.
- ISBN-13 978-1032125497
- Edition 1st
- Publisher CRC Press
- Publication date 1 September 2022
- Language English
- File size 14179 KB
- See all details
Kindle E-Readers
- Kindle (5th Generation)
- Kindle Keyboard
- Kindle (2nd Generation)
- Kindle (1st Generation)
- Kindle Paperwhite
- Kindle Paperwhite (5th Generation)
- Kindle Touch
- Kindle Voyage
- Kindle Oasis
Kindle Fire Tablets
- Kindle Fire HD 8.9"
- Kindle Fire HD(1st Generation)
- Kindle Fire
Free Kindle Reading Apps
- Kindle for Windows 8
- Kindle for Web
- Kindle for BlackBerry
- Kindle for Android
- Kindle for Android Tablets
- Kindle for iPhone
- Kindle for iPad
- Kindle for Mac
- Kindle for PC

Product description
About the author, product details.
- ASIN : B0B6WWPWM4
- Publisher : CRC Press; 1st edition (1 September 2022)
- Language : English
- File size : 14179 KB
- Simultaneous device usage : Up to 4 simultaneous devices, per publisher limits
- Text-to-Speech : Enabled
- Enhanced typesetting : Enabled
- X-Ray : Not Enabled
- Word Wise : Not Enabled
- Print length : 236 pages
- Page numbers source ISBN : 1032125497
About the author
Abbas kudrati.
Abbas Kudrati is a highly regarded cybersecurity expert and accomplished public speaker, currently serving as Microsoft Asia's Lead Chief Cybersecurity Advisor for the Security Solutions Area. In this role, he advises on cutting-edge cybersecurity strategies and technologies to ensure Microsoft's clients remain safe in an increasingly digital world.
Beyond his work at Microsoft, Abbas is a sought-after executive advisor to numerous prestigious organizations, including LaTrobe University, HITRUST ASIA, and EC Council ASIA. He also supports the broader security community through his work with ISACA Chapters and by mentoring students.
As a bestselling author, Abbas has written several authoritative books on cybersecurity, including "Threat Hunting in the Cloud" by Wiley, "Zero Trust and Journey Across the Digital Estate" by CRC Press, and "Managing Risks in Digital Transformation" by Packt. He is also the Technical Editor for two books, "Effective Crisis Management" by BPB and "IoT Security with Microsoft Defender for IoT" by Packt.
Abbas is also a highly respected part-time Professor of Practice at LaTrobe University and a keynote speaker on a range of cybersecurity-related topics, including Zero-Trust, Cloud Security, Governance, Risk, and Compliance. His extensive expertise in the field of cybersecurity and engaging speaking style make him a popular choice for events, conferences, and corporate training sessions.
His post-nominals include C|CISO, CISM, CISA, CDPSE, CGEIT, CSX-P, Cobit5, Forrester ZTS, MS900, SCI900, AZ900, MCSE, MCSA, CCNA, CEH, CHFI, ECRP, CCSK, ITIL(F), Prince2 Practitioner, ISO 27001 L.A.
https://www.linkedin.com/in/akudrati/
Customer reviews
- Sort reviews by Top reviews Most recent Top reviews
Top reviews from India
Top reviews from other countries.
Report an issue
- Press Releases
- Amazon Science
- Sell on Amazon
- Sell under Amazon Accelerator
- Protect and Build Your Brand
- Amazon Global Selling
- Become an Affiliate
- Fulfilment by Amazon
- Advertise Your Products
- Amazon Pay on Merchants
- COVID-19 and Amazon
- Your Account
- Returns Centre
- 100% Purchase Protection
- Amazon App Download
- Conditions of Use & Sale
- Privacy Notice
- Interest-Based Ads

Executive Summary: 2024 State of Zero Trust & Encryption Study
The state of zero trust and encryption in 2024.
The Entrust Cybersecurity Institute has partnered with the Ponemon Institute to survey over 4,000 IT and IT security practitioners across 10 countries, asking about their Zero Trust implementation practices. Read the Executive Summary to discover the key highlights from the study.
Download Full Report
Read summary.

By The Numbers
of respondents said risk of cyber breach is the No. 1 driver to implement Zero Trust
of respondents said hackers were their top worry related to the threat landscape
of global organizations have begun their Zero Trust journey
Related Resources
Why zero trust is a must for corporate governance.
Pursue Zero Trust strategies that align with both the NIST and CISA.
Entrust Cybersecurity Institute Podcast
Hiding in Plain Sight - Uncovering Cybersecurity's Hidden Risks
Zero Trust is a security policy that authenticates all users for secure access control. Discover Entrust’s Zero Trust solutions today.
Zero Trust Architecture: Building a Resilient Cybersecurity Framework with Key Technologies and Strategies
Today’s cybersecurity landscape has promoted zero trust to the top of the agenda for teams and CISOs alike. Nitin Uttreja, CISSP, shares his experience and a plan for implementing zero trust in an organization.

Imagine your network as a large corporate headquarters: a sprawling campus with multiple buildings. In the old days, the focus was on the main gate, checking badges as employees and visitors enter. But what if an intruder manages to sneak inside? That's the wake-up call zero trust brings to the table. It's not just about guarding the perimeter; It's about having security protocols at every door, elevator and server room – constant verification that each person is where they should be and accessing only what they need and are authorized to touch, at every moment they're on the premises.
As the name suggests, zero trust takes a “trust-no-one” approach, whether someone is accessing an application from inside or outside of the network. It’s about verifying everything – every user, every device – every time someone tries to access something.
Building a Defensible Security Architecture
Establishing a zero trust framework requires a strategy. And the key to this strategy is understanding the importance of safeguarding sensitive data and implementing rigorous access controls. I’m going to explain how, in my roles, I’ve navigated this paradigm shift towards zero trust security.
Define What to Protect
The first step in aligning with zero trust principles is understanding what needs protection. Cybercriminals are primarily motivated by financial gain, targeting data that carries value on the dark web. Determine what your organization's sensitive information and systems are – these are the assets that, if compromised, could cause significant damage. Prioritizing the protection of your most valuable assets is a critical step before you define the roadmap for zero trust architecture.
Locate Sensitive Data
Sensitive information may reside in various locations within an organization, such as laptops, servers, databases, and cloud solutions. Knowing where your sensitive data resides is critical in building a zero trust strategy.
Map the Transaction Flows
Understanding how data moves within your network, from one asset to another, is another key. Mapping transaction flows reveals the paths users and systems take to access data; knowing these has enabled me and my teams to develop targeted security measures.
Build and Implement a Zero Trust Policy
Develop and apply a zero trust policy that limits access to resources according to a strict need-to-know standard. You need to ensure robust authentication for all access efforts, to reinforce your network's defense against unauthorized access.
Log and Continuously Monitor
Forward all logs to a central location for anomaly detection and decrypt layer 7 traffic at gateways to inspect for malicious activity. This comprehensive approach is crucial for maintaining a zero trust framework.
Implementing Zero Trust: Key Solutions
In my experience, several technologies and strategies have been pivotal in transitioning organizations I’ve worked at towards a zero trust architecture. A few of them are as follows:
Network Access Control (NAC) NAC solutions can play a vital role in ensuring that devices connecting to the network are compliant with security policies. A NAC solution can authenticate and authorize endpoints, conduct security posture assessments to ensure devices are equipped with necessary protections like antivirus and disk encryption. Further integration with configuration management databases (CMDB) can enhance visibility into unmanaged devices.
Micro-Segmentation Flat networks tend to fail miserably. By contrast, micro-segmentation is a strategy to break down a network into smaller, more manageable zones, and to control east-west traffic with firewalls. Such an approach establishes protected areas within the network, preventing threats from propagating from one segment to another in the event of a breach.
Identity Creating a solid identity framework is pivotal in shaping a zero-trust architecture, integrating principles like the least privilege, role-based access control (RBAC), and multi-factor authentication (MFA). Define your RBAC with the minimum level of access, and users/systems should consume these roles to access resources. Subsequently, MFA adds an essential layer of security.
Secure Web Gateways (SWG) / Secure Access Service Edge (SASE) The shift to remote work has highlighted the limitations of traditional VPNs. SWGs and SASE solutions address these gaps by providing secure, direct-to-cloud connections, and – in my experience – have ensured that remote employees can access resources safely without the need for a VPN.
Privileged Access Management (PAM) The notion of privileged access management (PAM) plays a pivotal role in zero trust by addressing the security risks associated with privileged accounts. PAM ensures that only authorized users are able to access sensitive resources, minimizing the risk of unauthorized access.
Next-Generation Firewalls (NGFW) and Endpoint Detection and Response (EDR) NGFWs and EDR solutions can enhance the overall resilience and efficacy of a zero trust security framework, ensuring comprehensive protection against evolving cyber threats across the network and endpoints. NGFWs differ from and go beyond traditional firewalls by incorporating capabilities like deep packet inspection, application-level filtering, and threat intelligence integration. EDR solutions, meanwhile, provide real-time monitoring and response to threats on endpoints.
The reality is that zero trust is much more than just a buzzword. In fact, I’ve found it to be an effective security strategy against modern-day attacks. To transition your organization to zero trust, use the functionality of your existing security solutions and consider additional technologies for a comprehensive architecture. Embracing zero trust principles and architecture, you can proactively secure digital assets and sensitive data, and ensure resilience against evolving cyber threats.
Nitin Uttreja , CISSP, has over 15 years of specialized experience in cybersecurity. As Director, Global Cybersecurity at Estee Lauder, he currently spearheads the Security Architecture and Engineering team, where his responsibilities encompass the evaluation, design and deployment cybersecurity solutions.
- Support your continuing education with the ISC2 Zero Trust Architecture in the Cloud online training
- Zero Trust for Identity: Strategies and Leadership to Protect Businesses will help you develop valuable implementation skills
Microsoft’s transition to Zero Trust
Today’s cloud-based enterprise environments and always-on workforces require access to applications and resources that exist beyond the traditional boundaries of corporate networks, restrictive network firewalls and VPNs. Organizations are moving to modern, more holistic systems of verification to manage enterprise security and to combat threats differently.
Microsoft has adopted a modern approach to security called “Zero Trust,” which is based on the principle: never trust, always verify. This security approach protects our company and our customers by managing and granting access based on the continual verification of identities, devices and services. In this content suite, the Microsoft Digital team shares their strategic approach, best practices, and hands-on learning from our enterprise-wide transition to Zero Trust architecture.
Roadmap to Zero Trust
Although transitioning to Zero Trust is a multifaceted journey that can span many years, the architecture powerfully addresses the security challenges that modern enterprises face. Microsoft Digital knew that implementing Zero Trust would result in a notable shift in the way users access the corporate environment at Microsoft, so they created a layered approach to securing both corporate and customer data.
Microsoft Digital’s multistep implementation strategy is centered on strong user identity, device health verification, and secure, least-privilege access to corporate resources and services, all backed by rich data insights that reduce the risk of unauthorized lateral movement across the corporate network.
Through these authentication and verification methods, Microsoft Digital ensures that users are only given access that is explicitly authorized. Learn more about how Microsoft structured a phased approach to our Zero Trust implementation.
Microsoft Security offers guidance about how to optimize your Zero Trust strategy with an optimization model and solutions.
Featured content

Implementing a Zero Trust security model at Microsoft


Lessons learned at Microsoft: Five steps you can take to reduce your ransomware risk

Microsoft’s digital security team answers your Top 10 questions on Zero Trust

Zero Trust – Microsoft Security

Zero Trust solutions at Microsoft

Learning from engineering Zero Trust networking at Microsoft

Why Microsoft uses a playbook to guard against ransomware
Verifying identity.
The majority of security breaches today involve credential theft, and lapses in cyber hygiene amplify the potential for risk to employees and to organizations at large. That’s why one of the primary components of a Zero Trust system is the ability to verify a user’s identity before access is granted to the corporate network.
Microsoft Digital started by implementing multifactor authentication through the modern experience of Azure Authenticator.
This allows Microsoft to grant access to the specific corporate resources explicitly approved for each individual user, in a mobile-friendly environment and across multiple devices. As we continue to move forward, our end goal is to completely eliminate passwords. Learn more about the verifying identity phase of Microsoft’s Zero Trust journey.

Verifying identity in a Zero Trust model internally at Microsoft

Implementing strong user authentication with Windows Hello for Business

Microsoft’s CISO series: Eliminating passwords

Preparing your enterprise to eliminate passwords

The end of passwords, go passwordless

Managing user identities and secure access at Microsoft

Improving security by protecting elevated-privilege accounts at Microsoft

Using Azure Multi-Factor Authentication at Microsoft to enhance security
Verifying devices.
Because unmanaged devices are an easy entry point for bad actors, ensuring that only healthy devices can access critical applications and data is vital for enterprise security. As a fundamental part of our Zero Trust implementation, Microsoft Digital worked to enroll all user devices in device management systems.
Enabling device health verification in this way is essential to managing the policies that govern access to Microsoft resources.
Microsoft Digital uses either cloud management software like Microsoft Intune or classic on-premises management tools to ensure that every device is classified as healthy before allowing access to major productivity applications like Microsoft Exchange, SharePoint, and Teams. We also secure the millions of IoT devices in use with an integrated security controls strategy that incorporates comprehensive risk assessments and mitigation strategies at the intelligent edge. Learn more about the verifying device health phase of Microsoft’s Zero Trust journey.

Verifying device health at Microsoft with Zero Trust

Evolving the device experience at Microsoft

Managing Windows 10 devices with Microsoft Intune

Creating security controls for IoT devices at Microsoft
Verifying access.
Despite the focus on managing and maintaining device health throughout our enterprise environment, some scenarios—like vendor staffing, acquisitions, and guest projects—require users to work from unmanaged devices. With those situations in mind, the Microsoft Digital team defined a plan to minimize the means of access to corporate resources, and to require identity and device health verification for all access methods.
Microsoft Digital transitioned from a corporate network approach to internet-first access methods, with a final goal of internet-only access methods in sight. This strategy reduces users accessing the corporate network for most scenarios, and will enable Microsoft Digital’s plan to establish a set of managed virtualized services that make applications and full Windows desktop environments available to users with unmanaged devices. Learn more about the verifying access phase of Microsoft’s Zero Trust journey.

Using a Zero Trust strategy to secure Microsoft’s network during remote work

Understanding Microsoft’s approach to Zero Trust Networking with Microsoft Azure

Using shielded virtual machines to help protect high-value assets

Moving to next-generation SIEM at Microsoft with Microsoft Sentinel

Sharing how Microsoft now secures its network with a Zero Trust model

Building an anti-ransomware program at Microsoft focused on an Optimal Ransomware Resiliency State

Microsoft Azure Blog
Category: AI + Machine Learning • 11 min read
From code to production: New ways Azure helps you build transformational AI experiences chevron_right
By Jessica Hawk Corporate Vice President, Data, AI, and Digital Applications, Product Marketing
What was once a distant promise is now manifesting—and not only through the type of apps that are possible, but how you can build them. With Azure, we’re meeting you where you are today—and paving the way to where you’re going. So let’s jump right into some of what you’ll learn over the next few days. Welcome to Build 2024!
Unleashing innovation: The new era of compute powering Azure AI solutions chevron_right
By Omar Khan General Manager, Azure Product Marketing
New models added to the Phi-3 family, available on Microsoft Azure chevron_right
By Misha Bilenko Corporate Vice President, Microsoft GenAI
AI + Machine Learning , Announcements , Azure AI Content Safety , Azure AI Studio , Azure OpenAI Service , Partners
Published May 13, 2024 • 2 min read
Introducing GPT-4o: OpenAI’s new flagship multimodal model now in preview on Azure chevron_right
By Eric Boyd Corporate Vice President, Azure AI Platform, Microsoft
Microsoft is thrilled to announce the launch of GPT-4o, OpenAI’s new flagship model on Azure AI. This groundbreaking multimodal model integrates text, vision, and audio capabilities, setting a new standard for generative and conversational AI experiences.
AI + Machine Learning , Announcements , Azure AI , Azure Cosmos DB , Azure Kubernetes Service (AKS) , Azure Migrate , Azure Web PubSub , Compute , Industry trends
Published May 6, 2024 • 5 min read
Harnessing the power of intelligent apps through modernization chevron_right
By Mike Hulme GM, Azure Digital Applications Marketing
81% of organizations believe AI will give them a competitive edge. Applications are where AI comes to life. Intelligent applications, powered by AI and machine learning (ML) algorithms are pivotal to enhancing performance and stimulating growth. Thus, innovating with intelligent apps is crucial for businesses looking to gain competitive advantage and accelerate growth in this era of AI.
AI + Machine Learning , Announcements , Azure AI , Azure AI Search , Azure App Service , Azure Cosmos DB , Azure Database for PostgreSQL , Azure Databricks , Azure DevOps , Azure Health Data Services , Azure Machine Learning , Azure Managed Applications , Azure SQL Database , Customer stories , DevOps , Events , Microsoft Azure portal , Microsoft Copilot for Azure , Microsoft Defender for Cloud , Migration , SQL Server on Azure Virtual Machines
Published May 2, 2024 • 11 min read
What’s new in Azure Data, AI, and Digital Applications: Harness the power of intelligent apps chevron_right
Sharing insights on technology transformation along with important updates and resources about the data, AI, and digital application solutions that make Microsoft Azure the platform for the era of AI.
Hybrid + Multicloud , Thought leadership
Published May 2, 2024 • 4 min read
Cloud Cultures, Part 8: Recapturing the entrepreneurial spirit in the American Rust Belt chevron_right
By Corey Sanders Corporate Vice President, Microsoft Cloud for Industry
Excited to explore this industrious spirit and a cloud culture closer to home, we ventured to the Northeastern and Midwestern states—the famed Rust Belt—to learn how entrepreneurial adaptability is energizing both people and businesses in the area.
Latest posts
Analytics , Announcements , Azure Kubernetes Service (AKS) , Azure Monitor , Compute , Containers
Published June 5, 2024 • 4 min read
Announcing Advanced Container Networking Services for your Azure Kubernetes Service clusters chevron_right
By Deepak Bansal Corporate Vice President and Technical Fellow, Microsoft Azure , and Chandan Aggarwal Partner Group Engineering Manager, Microsoft Azure
Microsoft’s Azure Container Networking team is excited to announce a new offering called Advanced Container Networking Services. It’s a suite of services built on top of existing networking solutions for Azure Kubernetes Services (AKS) to address complex challenges around observability, security, and compliance.

AI + Machine Learning , Announcements , Azure Database for PostgreSQL , Azure Machine Learning , Azure OpenAI Service , Events , Migration
Published June 5, 2024 • 5 min read
Raise the bar on AI-powered app development with Azure Database for PostgreSQL chevron_right
By Ramnik Gulati Sr. Director, Product Marketing of Microsoft Operational Databases
By harnessing the might of PostgreSQL in the cloud—with all the scalability and convenience you expect—comes Microsoft Azure Database for PostgreSQL. This fully managed service takes the hassle out of managing your PostgreSQL instances, allowing you to focus on what really matters: building amazing, AI-powered applications.

AI + Machine Learning , Azure AI , Azure AI Services , Azure OpenAI Service , Cloud Services , Partners
Published June 4, 2024 • 10 min read
Unlock AI innovation with new joint capabilities from Microsoft and SAP chevron_right
By Silvio Bessa General Manager, SAP Business Unit
Learn more about the transformative synergy of the Microsoft Cloud and RISE with SAP for business.

AI + Machine Learning , Announcements , Azure VMware Solution , Migration , Partners
Published May 30, 2024 • 3 min read
Microsoft and Broadcom to support license portability for VMware Cloud Foundation on Azure VMware Solution chevron_right
By Brett Tanzer Vice President, Product Management
Microsoft and Broadcom are expanding our partnership with plans to support VMware Cloud Foundation subscriptions on Azure VMware Solution. Customers that own or purchase licenses for VMware Cloud Foundation will be able to use those licenses on Azure VMware Solution, as well as their own datacenters, giving them flexibility to meet changing business needs.

Announcements , Azure Bastion , Security
Published May 30, 2024 • 4 min read
Enhance your security capabilities with Azure Bastion Premium chevron_right
By Aaron Tsang Product Manager, Microsoft
Microsoft Azure Bastion, now in public preview, will provide advanced recording, monitoring, and auditing capabilities for customers handling highly sensitive workloads.
AI + Machine Learning , Azure AI , Azure AI Content Safety , Azure AI Search , Azure AI Studio , Azure Cosmos DB , Azure Kubernetes Service (AKS) , Azure OpenAI Service , Events
Published May 30, 2024 • 5 min read
Celebrating customers’ journeys to AI innovation at Microsoft Build 2024 chevron_right
By Victoria Sykes Product Marketing Manager, Azure AI, Microsoft
From enhancing productivity and creativity to revolutionizing customer interactions with custom copilots, our customers demonstrate the transformative power of generative AI and truly, brought Build 2024 to life. So, how’d they do it?

AI + Machine Learning , Industry trends , Thought leadership
Published May 29, 2024 • 4 min read
IT trends show customers need computing power to take advantage of AI chevron_right
In a recent study, Microsoft surveyed over 2,000 IT professionals across ten countries on their tech readiness for and adoption of AI as well as their concerns and challenges along the way.

AI + Machine Learning , Announcements , Azure Maps , Integration
Azure Maps: Reimagining location services with cloud and AI innovation chevron_right
By Nick Lee Corporate Vice President, Microsoft Maps and Local
Today, we’re announcing the unification of our enterprise maps offerings under Microsoft Azure Maps. This enables our customers to accelerate innovation by leveraging other Microsoft Azure cloud services while retaining many familiar features from Bing Maps for Enterprise.

AI + Machine Learning , Announcements , Azure AI , Azure AI Studio , Azure OpenAI Service , Events
Published May 21, 2024 • 5 min read
At Microsoft Build 2024, we are excited to add new models to the Phi-3 family of small, open models developed by Microsoft.
AI + Machine Learning , Announcements , Azure AI , Azure AI Content Safety , Azure AI Services , Azure AI Studio , Azure Cosmos DB , Azure Database for PostgreSQL , Azure Kubernetes Service (AKS) , Azure OpenAI Service , Azure SQL Database , Events
Published May 21, 2024 • 11 min read


McKinsey Technology Trends Outlook 2023
After a tumultuous 2022 for technology investment and talent, the first half of 2023 has seen a resurgence of enthusiasm about technology’s potential to catalyze progress in business and society. Generative AI deserves much of the credit for ushering in this revival, but it stands as just one of many advances on the horizon that could drive sustainable, inclusive growth and solve complex global challenges.
To help executives track the latest developments, the McKinsey Technology Council has once again identified and interpreted the most significant technology trends unfolding today. While many trends are in the early stages of adoption and scale, executives can use this research to plan ahead by developing an understanding of potential use cases and pinpointing the critical skills needed as they hire or upskill talent to bring these opportunities to fruition.
Our analysis examines quantitative measures of interest, innovation, and investment to gauge the momentum of each trend. Recognizing the long-term nature and interdependence of these trends, we also delve into underlying technologies, uncertainties, and questions surrounding each trend. This year, we added an important new dimension for analysis—talent. We provide data on talent supply-and-demand dynamics for the roles of most relevance to each trend. (For more, please see the sidebar, “Research methodology.”)
New and notable
All of last year’s 14 trends remain on our list, though some experienced accelerating momentum and investment, while others saw a downshift. One new trend, generative AI, made a loud entrance and has already shown potential for transformative business impact.
Research methodology
To assess the development of each technology trend, our team collected data on five tangible measures of activity: search engine queries, news publications, patents, research publications, and investment. For each measure, we used a defined set of data sources to find occurrences of keywords associated with each of the 15 trends, screened those occurrences for valid mentions of activity, and indexed the resulting numbers of mentions on a 0–1 scoring scale that is relative to the trends studied. The innovation score combines the patents and research scores; the interest score combines the news and search scores. (While we recognize that an interest score can be inflated by deliberate efforts to stimulate news and search activity, we believe that each score fairly reflects the extent of discussion and debate about a given trend.) Investment measures the flows of funding from the capital markets into companies linked with the trend. Data sources for the scores include the following:
- Patents. Data on patent filings are sourced from Google Patents.
- Research. Data on research publications are sourced from the Lens (www.lens.org).
- News. Data on news publications are sourced from Factiva.
- Searches. Data on search engine queries are sourced from Google Trends.
- Investment. Data on private-market and public-market capital raises are sourced from PitchBook.
- Talent demand. Number of job postings is sourced from McKinsey’s proprietary Organizational Data Platform, which stores licensed, de-identified data on professional profiles and job postings. Data is drawn primarily from English-speaking countries.
In addition, we updated the selection and definition of trends from last year’s study to reflect the evolution of technology trends:
- The generative-AI trend was added since last year’s study.
- We adjusted the definitions of electrification and renewables (previously called future of clean energy) and climate technologies beyond electrification and renewables (previously called future of sustainable consumption).
- Data sources were updated. This year, we included only closed deals in PitchBook data, which revised downward the investment numbers for 2018–22. For future of space technologies investments, we used research from McKinsey’s Aerospace & Defense Practice.
This new entrant represents the next frontier of AI. Building upon existing technologies such as applied AI and industrializing machine learning, generative AI has high potential and applicability across most industries. Interest in the topic (as gauged by news and internet searches) increased threefold from 2021 to 2022. As we recently wrote, generative AI and other foundational models change the AI game by taking assistive technology to a new level, reducing application development time, and bringing powerful capabilities to nontechnical users. Generative AI is poised to add as much as $4.4 trillion in economic value from a combination of specific use cases and more diffuse uses—such as assisting with email drafts—that increase productivity. Still, while generative AI can unlock significant value, firms should not underestimate the economic significance and the growth potential that underlying AI technologies and industrializing machine learning can bring to various industries.
Investment in most tech trends tightened year over year, but the potential for future growth remains high, as further indicated by the recent rebound in tech valuations. Indeed, absolute investments remained strong in 2022, at more than $1 trillion combined, indicating great faith in the value potential of these trends. Trust architectures and digital identity grew the most out of last year’s 14 trends, increasing by nearly 50 percent as security, privacy, and resilience become increasingly critical across industries. Investment in other trends—such as applied AI, advanced connectivity, and cloud and edge computing—declined, but that is likely due, at least in part, to their maturity. More mature technologies can be more sensitive to short-term budget dynamics than more nascent technologies with longer investment time horizons, such as climate and mobility technologies. Also, as some technologies become more profitable, they can often scale further with lower marginal investment. Given that these technologies have applications in most industries, we have little doubt that mainstream adoption will continue to grow.
Organizations shouldn’t focus too heavily on the trends that are garnering the most attention. By focusing on only the most hyped trends, they may miss out on the significant value potential of other technologies and hinder the chance for purposeful capability building. Instead, companies seeking longer-term growth should focus on a portfolio-oriented investment across the tech trends most important to their business. Technologies such as cloud and edge computing and the future of bioengineering have shown steady increases in innovation and continue to have expanded use cases across industries. In fact, more than 400 edge use cases across various industries have been identified, and edge computing is projected to win double-digit growth globally over the next five years. Additionally, nascent technologies, such as quantum, continue to evolve and show significant potential for value creation. Our updated analysis for 2023 shows that the four industries likely to see the earliest economic impact from quantum computing—automotive, chemicals, financial services, and life sciences—stand to potentially gain up to $1.3 trillion in value by 2035. By carefully assessing the evolving landscape and considering a balanced approach, businesses can capitalize on both established and emerging technologies to propel innovation and achieve sustainable growth.
Tech talent dynamics
We can’t overstate the importance of talent as a key source in developing a competitive edge. A lack of talent is a top issue constraining growth. There’s a wide gap between the demand for people with the skills needed to capture value from the tech trends and available talent: our survey of 3.5 million job postings in these tech trends found that many of the skills in greatest demand have less than half as many qualified practitioners per posting as the global average. Companies should be on top of the talent market, ready to respond to notable shifts and to deliver a strong value proposition to the technologists they hope to hire and retain. For instance, recent layoffs in the tech sector may present a silver lining for other industries that have struggled to win the attention of attractive candidates and retain senior tech talent. In addition, some of these technologies will accelerate the pace of workforce transformation. In the coming decade, 20 to 30 percent of the time that workers spend on the job could be transformed by automation technologies, leading to significant shifts in the skills required to be successful. And companies should continue to look at how they can adjust roles or upskill individuals to meet their tailored job requirements. Job postings in fields related to tech trends grew at a very healthy 15 percent between 2021 and 2022, even though global job postings overall decreased by 13 percent. Applied AI and next-generation software development together posted nearly one million jobs between 2018 and 2022. Next-generation software development saw the most significant growth in number of jobs (exhibit).
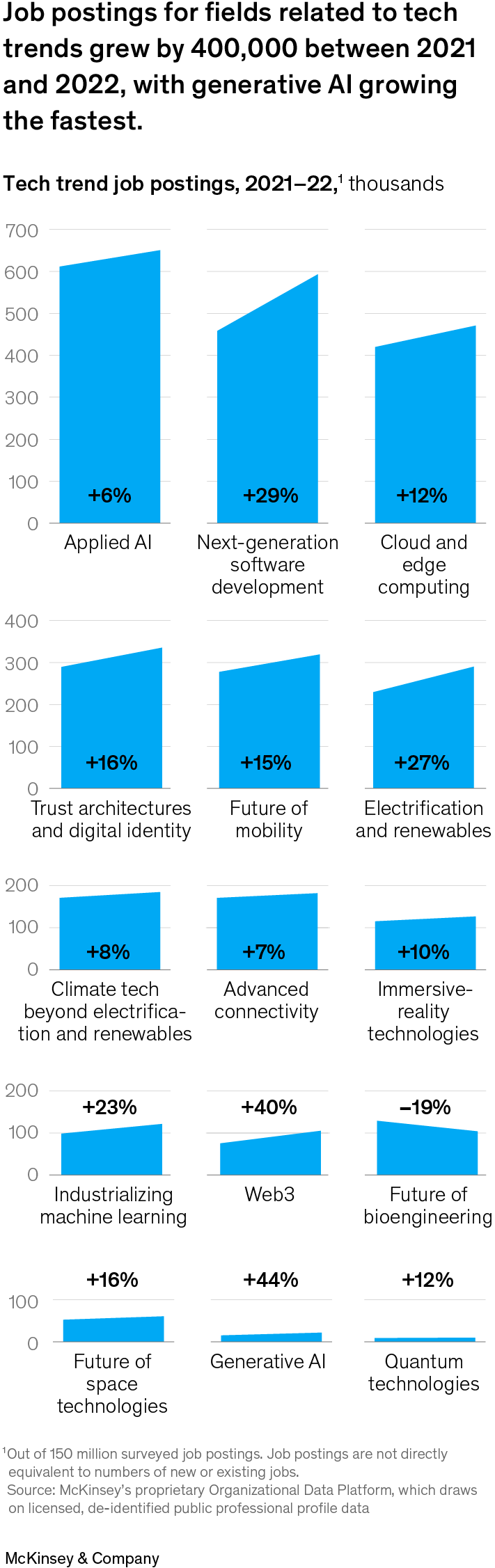
Image description:
Small multiples of 15 slope charts show the number of job postings in different fields related to tech trends from 2021 to 2022. Overall growth of all fields combined was about 400,000 jobs, with applied AI having the most job postings in 2022 and experiencing a 6% increase from 2021. Next-generation software development had the second-highest number of job postings in 2022 and had 29% growth from 2021. Other categories shown, from most job postings to least in 2022, are as follows: cloud and edge computing, trust architecture and digital identity, future of mobility, electrification and renewables, climate tech beyond electrification and renewables, advanced connectivity, immersive-reality technologies, industrializing machine learning, Web3, future of bioengineering, future of space technologies, generative AI, and quantum technologies.
End of image description.
This bright outlook for practitioners in most fields highlights the challenge facing employers who are struggling to find enough talent to keep up with their demands. The shortage of qualified talent has been a persistent limiting factor in the growth of many high-tech fields, including AI, quantum technologies, space technologies, and electrification and renewables. The talent crunch is particularly pronounced for trends such as cloud computing and industrializing machine learning, which are required across most industries. It’s also a major challenge in areas that employ highly specialized professionals, such as the future of mobility and quantum computing (see interactive).
Michael Chui is a McKinsey Global Institute partner in McKinsey’s Bay Area office, where Mena Issler is an associate partner, Roger Roberts is a partner, and Lareina Yee is a senior partner.
The authors wish to thank the following McKinsey colleagues for their contributions to this research: Bharat Bahl, Soumya Banerjee, Arjita Bhan, Tanmay Bhatnagar, Jim Boehm, Andreas Breiter, Tom Brennan, Ryan Brukardt, Kevin Buehler, Zina Cole, Santiago Comella-Dorda, Brian Constantine, Daniela Cuneo, Wendy Cyffka, Chris Daehnick, Ian De Bode, Andrea Del Miglio, Jonathan DePrizio, Ivan Dyakonov, Torgyn Erland, Robin Giesbrecht, Carlo Giovine, Liz Grennan, Ferry Grijpink, Harsh Gupta, Martin Harrysson, David Harvey, Kersten Heineke, Matt Higginson, Alharith Hussin, Tore Johnston, Philipp Kampshoff, Hamza Khan, Nayur Khan, Naomi Kim, Jesse Klempner, Kelly Kochanski, Matej Macak, Stephanie Madner, Aishwarya Mohapatra, Timo Möller, Matt Mrozek, Evan Nazareth, Peter Noteboom, Anna Orthofer, Katherine Ottenbreit, Eric Parsonnet, Mark Patel, Bruce Philp, Fabian Queder, Robin Riedel, Tanya Rodchenko, Lucy Shenton, Henning Soller, Naveen Srikakulam, Shivam Srivastava, Bhargs Srivathsan, Erika Stanzl, Brooke Stokes, Malin Strandell-Jansson, Daniel Wallance, Allen Weinberg, Olivia White, Martin Wrulich, Perez Yeptho, Matija Zesko, Felix Ziegler, and Delphine Zurkiya.
They also wish to thank the external members of the McKinsey Technology Council.
This interactive was designed, developed, and edited by McKinsey Global Publishing’s Nayomi Chibana, Victor Cuevas, Richard Johnson, Stephanie Jones, Stephen Landau, LaShon Malone, Kanika Punwani, Katie Shearer, Rick Tetzeli, Sneha Vats, and Jessica Wang.
Explore a career with us
Related articles.

McKinsey Technology Trends Outlook 2022

Value creation in the metaverse

Quantum computing funding remains strong, but talent gap raises concern
Zero Trust Journey Across the Digital Estate by Abbas Kudrati, Binil A. Pillai
Get full access to Zero Trust Journey Across the Digital Estate and 60K+ other titles, with a free 10-day trial of O'Reilly.
There are also live events, courses curated by job role, and more.
Chapter 7 Future Horizon of Zero Trust
DOI: 10.1201/9781003225096-11
Trust is a human emotion and is the single greatest vulnerability when we think about cyber security. Given the interconnected and complex world we live in, if we stop assuming a level of trust and start challenging everyone inside and outside of our ecosystem, we can improve security. Nicola Nicol , industry expert
Organizations are all-in with the Zero Trust strategy, and decision makers say it will continue to be the top security priority over the years. Moreover, the relative importance of the Zero Trust strategy as a security initiative is projected to increase by 2023, as security decision makers anticipate that the strategy will remain critical to overall ...
Get Zero Trust Journey Across the Digital Estate now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.
Don’t leave empty-handed
Get Mark Richards’s Software Architecture Patterns ebook to better understand how to design components—and how they should interact.
It’s yours, free.

Check it out now on O’Reilly
Dive in for free with a 10-day trial of the O’Reilly learning platform—then explore all the other resources our members count on to build skills and solve problems every day.


IMAGES
VIDEO
COMMENTS
This book seeks to provide an end-to-end view of the Zero Trust approach across organizations' digital estates that includes strategy, business imperatives, architecture, solutions, human elements, and implementation approaches that could significantly enhance these organizations' success in learning, adapting, and implementing Zero Trust.
This book seeks to provide an end-to-end view of the Zero Trust approach across organizations' digital estates that includes strategy, business imperatives, architecture, solutions, human elements, and implementation approaches that could significantly enhance these organizations' success in learning, adapting, and implementing Zero Trust.
Title: Zero Trust Journey Across the Digital Estate. Author (s): Abbas Kudrati, Binil A. Pillai. Release date: September 2022. Publisher (s): CRC Press. ISBN: 9781000646344. The book provides an end-to-end view of the Zero Trust approach across organizations' digital estates that includes Strategy, Business Imperatives, Architecture, Solutions ...
This book seeks to provide an end-to-end view of the Zero Trust approach across organizations' digital estates that includes strategy, business imperatives, architecture, solutions, human elements, and implementation approaches that could significantly enhance these organizations' success in learning, adapting, and implementing Zero Trust.
This book seeks to provide an end-to-end view of the Zero Trust approach across organizations' digital estates that includes strategy, business imperatives, architecture, solutions, human elements, and implementation approaches that could significantly enhance these organizations' success in learning, adapting, and implementing Zero Trust.
Zero Trust Journey Across the Digital Estate - Ebook written by Abbas Kudrati, Binil A. Pillai. Read this book using Google Play Books app on your PC, android, iOS devices. Download for offline reading, highlight, bookmark or take notes while you read Zero Trust Journey Across the Digital Estate.
Buy Zero Trust Journey Across the Digital Estate 1 by Kudrati, Abbas, Pillai, Binil A. (ISBN: 9781032125497) from Amazon's Book Store. Everyday low prices and free delivery on eligible orders. Zero Trust Journey Across the Digital Estate: Amazon.co.uk: Kudrati, Abbas, Pillai, Binil A.: 9781032125497: Books
This book seeks to provide an end-to-end view of the Zero Trust approach across organizations' digital estates that includes strategy, business imperatives, architecture, solutions, human elements, and implementation approaches that could significantly enhance these organizations' success in learning, adapting, and implementing Zero Trust.
Get full access to Zero Trust Journey Across the Digital Estate and 60K+ other titles, with a free 10-day trial of O'Reilly. There are also live events, courses curated by job role, and more. Start your free trial. Chapter 1 History of and Introduction to Zero Trust. DOI: 10.1201/9781003225096-3.
The book provides an end-to-end view of the Zero Trust approach across organization's digital estates that includes strategy, business imperatives, architecture, solutions, human elements, and implementation approach that could significantly benefit large, small, and medium enterprises that want to learn adapt and implement Zero Trust. It ...
Zero Trust Journey Across the Digital Estate. 1st Edition. by Abbas Kudrati (Author), Binil A. Pillai (Author) 5.0 6 ratings. See all formats and editions. "Zero Trust is the strategy that organizations need to implement to stay ahead of cyber threats, period. The industry has 30 plus years of categorical failure that shows us that our past ...
Zero Trust Journey Across the Digital Estate Paperback - Import, 1 September 2022 by Abbas Kudrati (Author), Binil A. Pillai (Author) 5.0 5.0 out of 5 stars 5 ratings
This book seeks to provide an end-to-end view of the Zero Trust approach across organizations' digital estates that includes strategy, business imperatives, architecture, solutions, human elements, and implementation approaches that could significantly enhance these organizations' success in learning, adapting, and implementing Zero Trust ...
Zero Trust Journey Across the Digital Estate ebook By Abbas Kudrati. Read a Sample. Sign up to save your library. With an OverDrive account, you can save your favorite libraries for at-a-glance information about availability. Find out more about OverDrive accounts. Save Not today. Format. ebook. ISBN. 9781032125480. Author ...
This book seeks to provide an end-to-end view of the Zero Trust approach across organizations' digital estates that includes strategy, business imperatives, architecture, solutions, human elements, and implementation approaches that could significantly enhance these organizations' success in learning, adapting, and implementing Zero Trust.
"Zero Trust Journey Across the Digital Estate" is an information dense coverage of the security framework that has been evolving over the last 20 years and is now emerging as a recognised way to secure modern enterprise environments. This is not a primer for the executive team, although the CIO, CTO, CISO and IT leaders should definitely ...
Zero Trust Journey Across the Digital Estate: Kudrati, Abbas, Pillai, Binil A.: 9781032125497: Books - Amazon.ca
Zero Trust Journey Across the Digital Estate eBook : Kudrati, Abbas, Pillai, Binil A.: Amazon.in: Kindle Store
In their book on the "Zero Trust Journey Across the Digital Estate," Abbas Kudrati and Binil Pillai explore Zero Trust with a focus on the Microsoft model. One of their primary messages is that ...
The State of Zero Trust and Encryption in 2024. The Entrust Cybersecurity Institute has partnered with the Ponemon Institute to survey over 4,000 IT and IT security practitioners across 10 countries, asking about their Zero Trust implementation practices. Read the Executive Summary to discover the key highlights from the study.
Build and Implement a Zero Trust Policy. Develop and apply a zero trust policy that limits access to resources according to a strict need-to-know standard. You need to ensure robust authentication for all access efforts, to reinforce your network's defense against unauthorized access. Log and Continuously Monitor
Get Zero Trust Journey Across the Digital Estate now with the O'Reilly learning platform. O'Reilly members experience books, live events, courses curated by job role, and more from O'Reilly and nearly 200 top publishers. Start your free trial. Index Note: Boldface page references indicate tables. Italic references indicate figures and ...
The shift to a more mobile, cloud-connected workforce introduced new and continuously evolving security threats. All these factors have contributed to Zero Trust as the new standard in access architecture. In this content suite, Microsoft Digital shares their strategic approach and lessons learned from our enterprise-wide transition to Zero Trust architecture.
We're the largest global owner and operator of digital infrastructure, data center and connectivity infrastructure, supporting 5,000 customers across 50-plus metropolitan areas on six continents ...
By Jessica Hawk Corporate Vice President, Data, AI, and Digital Applications, Product Marketing. Sharing insights on technology transformation along with important updates and resources about the data, AI, and digital application solutions that make Microsoft Azure the platform for the era of AI. Hybrid + Multicloud, Thought leadership.
After a tumultuous 2022 for technology investment and talent, the first half of 2023 has seen a resurgence of enthusiasm about technology's potential to catalyze progress in business and society.Generative AI deserves much of the credit for ushering in this revival, but it stands as just one of many advances on the horizon that could drive sustainable, inclusive growth and solve complex ...
Chapter 7 Future Horizon of Zero Trust DOI: 10.1201/9781003225096-11 Trust is a human emotion and is the single greatest vulnerability when we think about cyber security. Given the interconnected and … - Selection from Zero Trust Journey Across the Digital Estate [Book]